Authors: Julien Vanwambeke, Functional Architect, Gaia-X and Vincent Kelleher, Software Engineer, Gaia-X
Introduction
You have just landed and cannot wait to rush into the sea 🌊 to start your holidays 🏝️ ️. But you first must go through the Customs 👮♂️. Hopefully, you are very organised, and you just give an envelope containing all your family’s passports, thus easing the identity-checking process.
In information technology, identity checks are often required. But how can you do that in a trustful way?
What are credentials?
Let us start with some definitions.
Credentials are “a letter or certificate that proves their identity or qualifications” (Collins Dictionary).
In the example above, your passport can be considered a credential since it proves your identity.
In information technology, a credential is “a piece of information that is sent from one computer to another to check that a user is who they claim to be or to allow someone to see information” (Cambridge Dictionary).
Credentials are thus used for authentication and authorisation purposes.
And you already know many credentials in your everyday life:
- The login/password you use to get connected to your favourite website.
- Your fingerprint to access your bank application on your phone.
- A token, retrieved after an OAuth authentication, to enable an API call.
As you can see, credentials are everywhere, in real or digital life.
But can you trust them?
For example, a passport can be a fake one. If you do not have the checking system used by the Customs, you can easily be fooled.
In the world of Data, this is the same: how can you trust the provider of a service offering or a data product?
The answer is easy: use Gaia-X de facto standards!
So, relax, put some sunscreen on 🧴, and let us travel 🛫 to the country of verifiable credentials and presentations.
Gaia-X and Verifiable Credentials
Verifiable credentials are an extension of standard credentials defined by W3C, adding “technologies, such as digital signatures. [It] makes verifiable credentials more tamper-evident and more trustworthy than their physical counterparts” (W3C), even if they only target authentication purposes.
In other words, verifiable credentials are credentials providing:
- Cryptographic mechanisms to prove that the claim(s) were not tampered.
- Information related to identifying the issuing authority (for example, a city government, national agency, natural person, conformity assessment body).
This is as if the way to check a passport has not been tampered was included inside the passport itself.
The verifiable credentials data model adds additional information related to:
- identifying the subject of the credential (for example, a photo, name, or identification number).
- the type of credential (for example, a Dutch passport, an American driving license, or a health insurance card).
- specific attributes or properties being asserted by the issuing authority about the subject (for example, nationality, the classes of vehicle entitled to drive, or date of birth).
- how the credential was derived.
- constraints on the credential (for example, validity period, or terms of use).
Keep also in mind that a verifiable credential can be signed by another entity other than the one concerned by the credential.
If you want to have more information about verifiable credentials, feel free to read W3C publication.
But now, how is Gaia-X using this standard?
Again, the answer is easy: EVERYWHERE!
Verifiable credentials are a pillar of the Gaia-X architecture, for example:
- Gaia-X Compliance engine, included in all Gaia-X Digital Clearing Houses, is issuing verifiable credentials, also known as Gaia-X Credentials, to certify that the requestor is trusted:
- For legal participants.
- For service offerings or data products.
- Gaia-X Catalogues requires Gaia-X credentials to:
- Enable a provider to publish its services offerings or data products.
- Enable a consumer to browse a catalogue (depending on the catalogue rules).
- Gaia-X Policy reasoning engine to:
- Use these credentials for access/usage control.
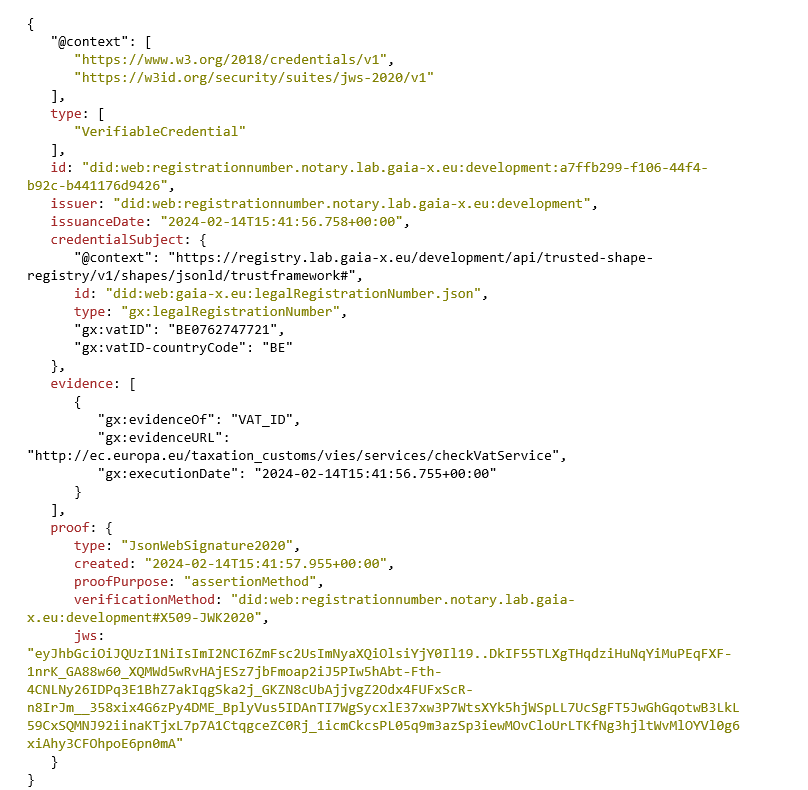
And now, put your sunglasses on 😎, and admire an example of a verifiable credential:
As you can see, the main components of a verifiable credential are the following ones:
- @context, which contains a list of URIs that resolve to what could be considered as descriptions of the types used in the verifiable credential.
- type which describes the types of the verifiable credential, multiple types can be defined, and this should always contain “VerifiableCredential”.
- issuer that identifies the document emitter
- credentialSubject which contains the credentials business information.
- proof the most important element that allows this verifiable credential to differentiate itself from a basic JSON-LD
Gaia-X and Verifiable Presentation
You are now familiar with the concept of verifiable credentials.
But, at some point, you could be flooded with them. For example, if you are a service provider, with a hundred services, you will need one Gaia-X Legal Participant Verifiable Credential for your company, and then a hundred of Gaia-X Service Offering Verifiable Credentials, one for each service offering. Dealing with them could then become tricky.
To ease the process, Gaia-X had the same idea you did when you wanted to travel: share all your family passports by putting them into an envelope ✉️.
Gaia-X is doing the same with verifiable credentials using the concept of verifiable presentation.
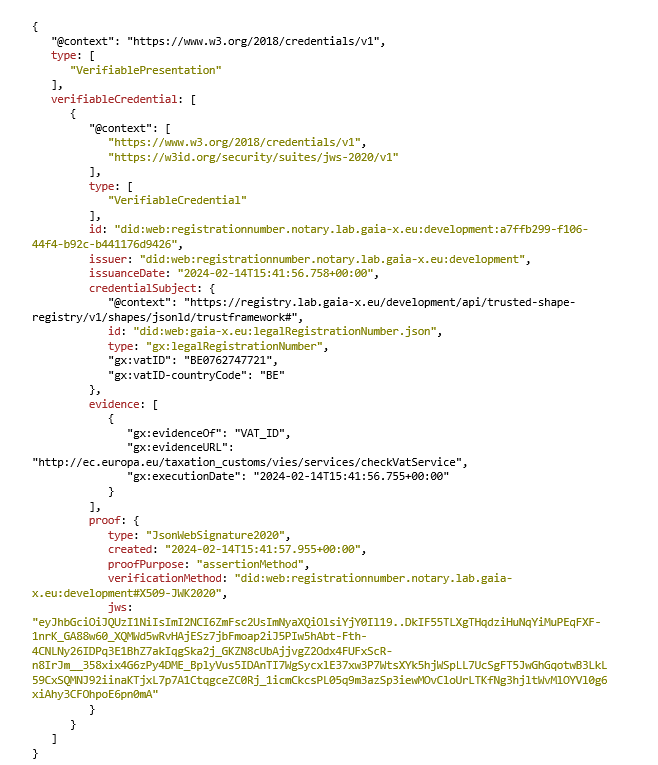
A verifiable presentation “can express data from multiple verifiable credentials and contain arbitrary additional data encoded as JSON-LD. They are used by a holder to present claims to a verifier” (W3C).
All the verifiable credentials inside a verifiable presentation can be issued by different entities, but are linked to the same subject, “typically expressing an aspect of person, organisation or entity” (W3C).
It is composed of:
- Presentation Metadata (id, type, holder, etc.).
- A list of Verifiable Credentials.
- A list of Proofs.
Verifiable presentations are used in Gaia-X as inputs of the Gaia-X Compliance engine.
Going back to the previous example, you are then sending one verifiable presentation including 101 verifiable credentials (one for your company and a 100 for your service offerings), and the Gaia-X Compliance engine will generate a Gaia-X Verifiable Credential (if you are compliant obviously).
Although most elements are borrowed from verifiable credentials, verifiable presentations differ because:
- They use a list of types with “VerifiablePresentation” and maybe other verifiable presentation types.
- The credentialSubject attribute is replaced by a verifiableCredential attribute which contains all the verifiable credentials that need to be presented.
- The proof attribute is optional here as the included verifiable credentials are all signed with their proof. Each proof can be issued by a different entity with different signing methods.
Conclusion
Gaia-X uses verifiable credentials and verifiable presentation standards from W3C to build its trust framework, to enable smooth communication between providers, consumers, Catalogues, and the Gaia-X Digital Clearing Houses.
As you may have noticed, you can easily get flooded with the number of credentials (yours and Gaia-X generated ones). But no worries, you can use Wallets 👛 to store them.
If you want to know more about Gaia-X and the way it is interacting with wallets, stay tuned!